Threat Hunting - Simplifying The Beacon Analysis Process - Active
By A Mystery Man Writer
Last updated 17 Jun 2024
In part one of this two-part series, I described what is involved with performing a beacon analysis and why it is so important […]
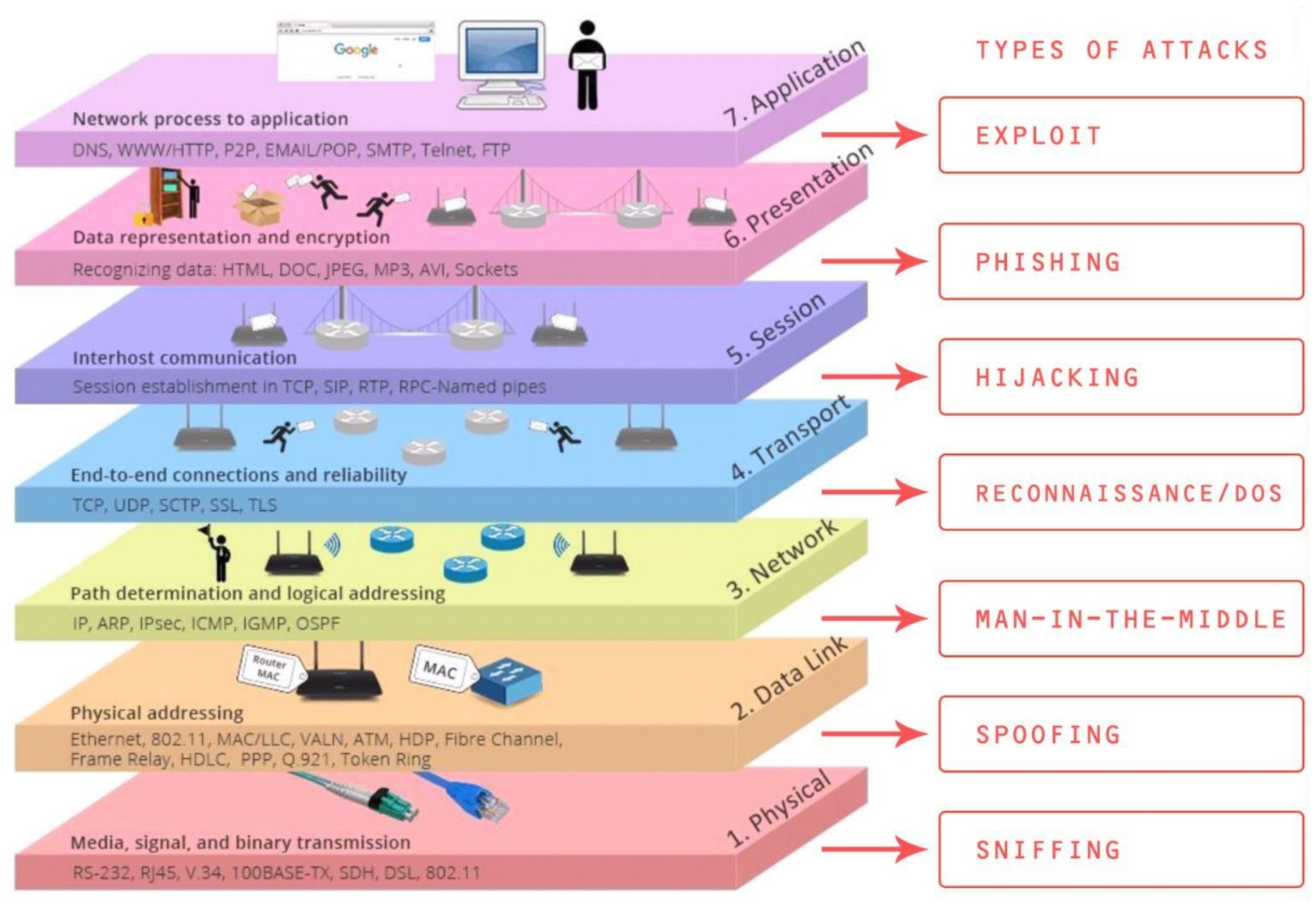
Symmetry, Free Full-Text

Process Injection Techniques - Cynet
Contact Tracing with Low Power Beacons for Active and Passive Data Management and Klika Tech Case Study
Threat Simulator - Active Countermeasures

From BumbleBee to Cobalt Strike: Steps of a BumbleBee intrusion
Threat Hunting - Simplifying The Beacon Analysis Process - Active Countermeasures
Beacon Analysis - The Key to Cyber Threat Hunting - Active Countermeasures

ICS Threat Hunting - They're Shootin' at the Lights! - Part 1

From BumbleBee to Cobalt Strike: Steps of a BumbleBee intrusion
Recommended for you
-
 Be the Beacon (Ladies' Power Lunch Transformation Anthologies)17 Jun 2024
Be the Beacon (Ladies' Power Lunch Transformation Anthologies)17 Jun 2024 -
 Beacon GoGuardian17 Jun 2024
Beacon GoGuardian17 Jun 2024 -
 Command Beacon17 Jun 2024
Command Beacon17 Jun 2024 -
Elite Consulting Study Abroad Program17 Jun 2024
-
About Beacon17 Jun 2024
-
 Beacon Specialized Living - Achieve Your Best Life17 Jun 2024
Beacon Specialized Living - Achieve Your Best Life17 Jun 2024 -
 MX908 Beacon Area Monitoring Device17 Jun 2024
MX908 Beacon Area Monitoring Device17 Jun 2024 -
 Some beacon designs I was playing around with earlier today. (from17 Jun 2024
Some beacon designs I was playing around with earlier today. (from17 Jun 2024 -
 Nonprofit Local News17 Jun 2024
Nonprofit Local News17 Jun 2024 -
 Camping Beacon Light, Hanging Camping Lantern17 Jun 2024
Camping Beacon Light, Hanging Camping Lantern17 Jun 2024
You may also like
-
 PandaHall Elite Magic Book Wax Seal Stamp, Hogwarts Sealing Wax17 Jun 2024
PandaHall Elite Magic Book Wax Seal Stamp, Hogwarts Sealing Wax17 Jun 2024 -
 PVA Is Plastic (and Used in Laundry Sheets and Pods) — Meliora Cleaning Products17 Jun 2024
PVA Is Plastic (and Used in Laundry Sheets and Pods) — Meliora Cleaning Products17 Jun 2024 -
 Tutorial Diy Cookie Scribe Read Cara & Co's Craft Blog – Cara & Co.17 Jun 2024
Tutorial Diy Cookie Scribe Read Cara & Co's Craft Blog – Cara & Co.17 Jun 2024 -
 Lamb Shank — Cold Spring Farm17 Jun 2024
Lamb Shank — Cold Spring Farm17 Jun 2024 -
 Arteza Gouache Art Paint Set, Neon Tones, 12ml - 12 Pack17 Jun 2024
Arteza Gouache Art Paint Set, Neon Tones, 12ml - 12 Pack17 Jun 2024 -
 20 oz Skinny Tumbler, Navy, Light Blue, and White Paint, Football, Grunge, Team Colors, PNG Sublimation Design, Instant Digital Download, Mockup17 Jun 2024
20 oz Skinny Tumbler, Navy, Light Blue, and White Paint, Football, Grunge, Team Colors, PNG Sublimation Design, Instant Digital Download, Mockup17 Jun 2024 -
 Scented Wax Warmer Melts and No-Mess Fragrance Tart™ Refills – The Gift of Scent17 Jun 2024
Scented Wax Warmer Melts and No-Mess Fragrance Tart™ Refills – The Gift of Scent17 Jun 2024 -
 Cowgirl Hats, Womens Western Hats17 Jun 2024
Cowgirl Hats, Womens Western Hats17 Jun 2024 -
 TIBSA | Paquete de 3 madejas 100g c/u | Estambre para crochet | Estambres para tejer ofertas | Yarn estambre grueso | Estambres para tejer | Estambres17 Jun 2024
TIBSA | Paquete de 3 madejas 100g c/u | Estambre para crochet | Estambres para tejer ofertas | Yarn estambre grueso | Estambres para tejer | Estambres17 Jun 2024 -
 chocolate & candy making - Whisk17 Jun 2024
chocolate & candy making - Whisk17 Jun 2024
