Token tactics: How to prevent, detect, and respond to cloud token
By A Mystery Man Writer
Last updated 02 Jun 2024


Protecting Prospects: How Darktrace Detected an Account Hijack
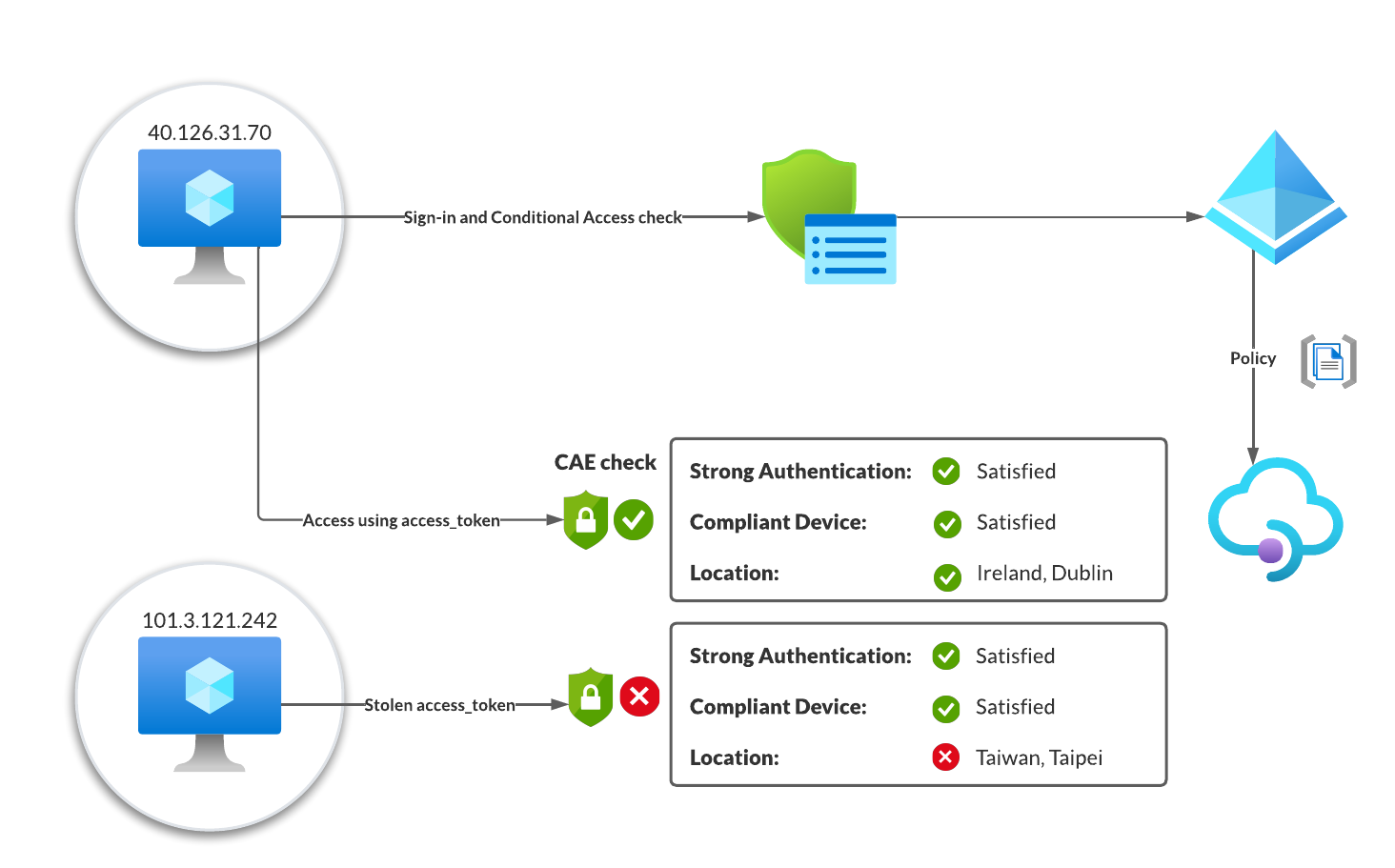
Continuous access evaluation - Cloudbrothers
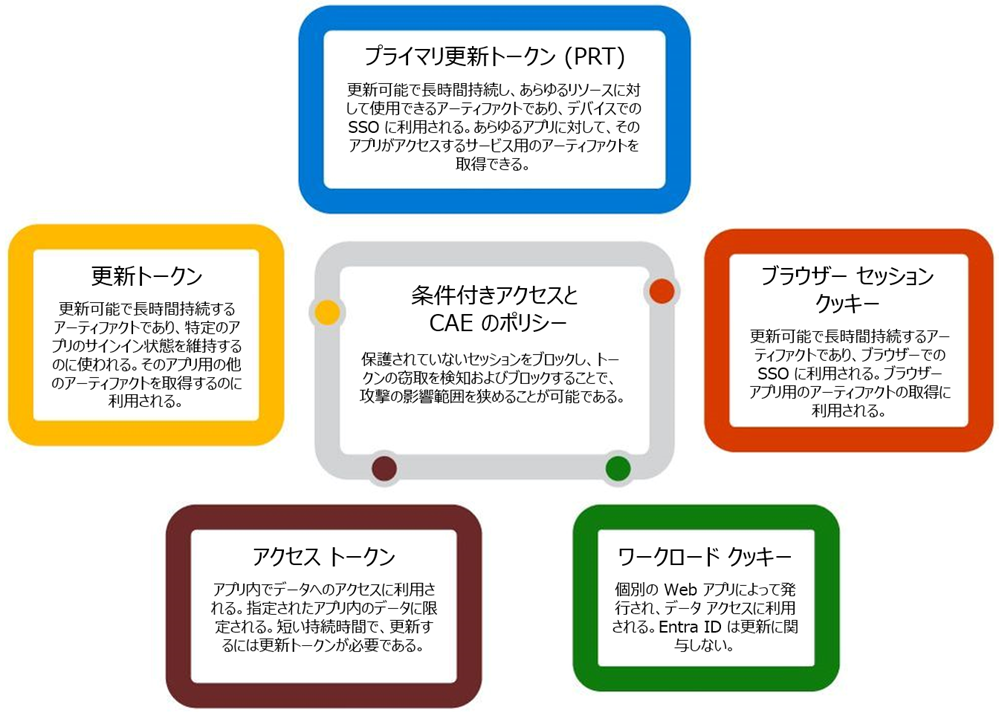
データ流出への対応: トークンの窃取について
Microsoft Detection and Response Team (DART) Archives - ThreatsHub Cybersecurity News
Updated: Bypassing Microsoft Token Protection, by Root ♊

Protecting Prospects: How Darktrace Detected an Account Hijack

Swedish Windows Security User Group » Threat protection

Office 365 shell WCSS Attack – Saas Alerts

Elli Shlomo (IR) 🇮🇱 on LinkedIn: #informationsecurity

GCP OAuth Token Hijacking in Google Cloud—Part 2 - Netskope
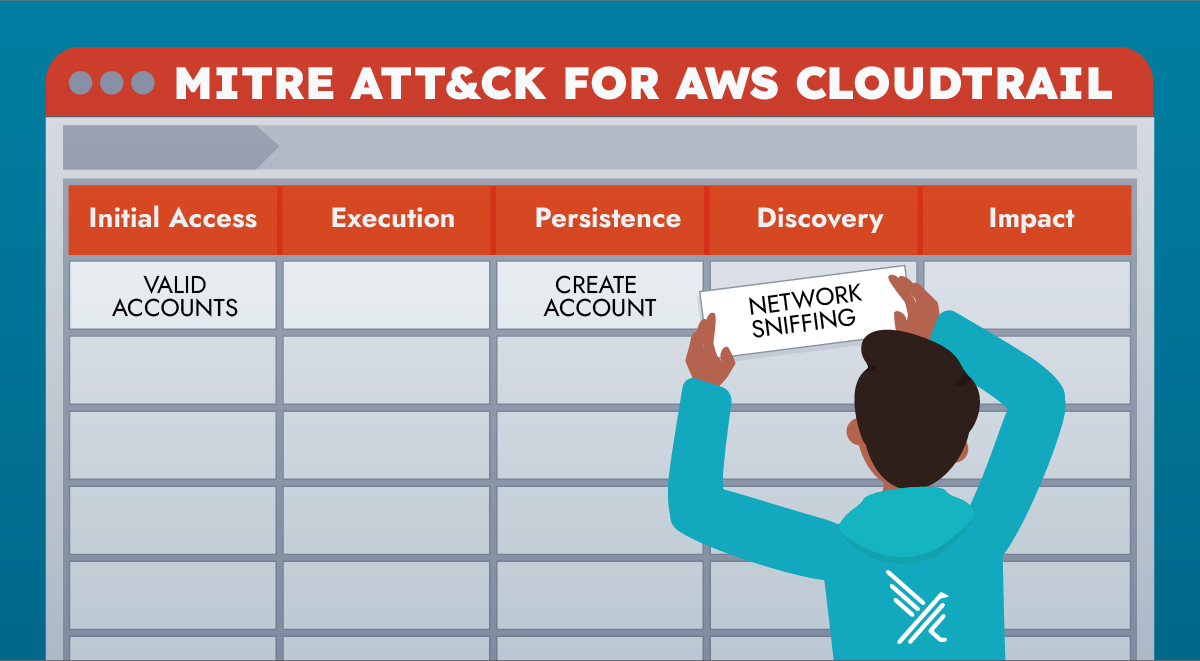
Aligning Falco's Cloudtrail Rules with MITRE ATT&CK – Sysdig

QakNote Infections: A Network-Based Exploration of Varied Attack Paths
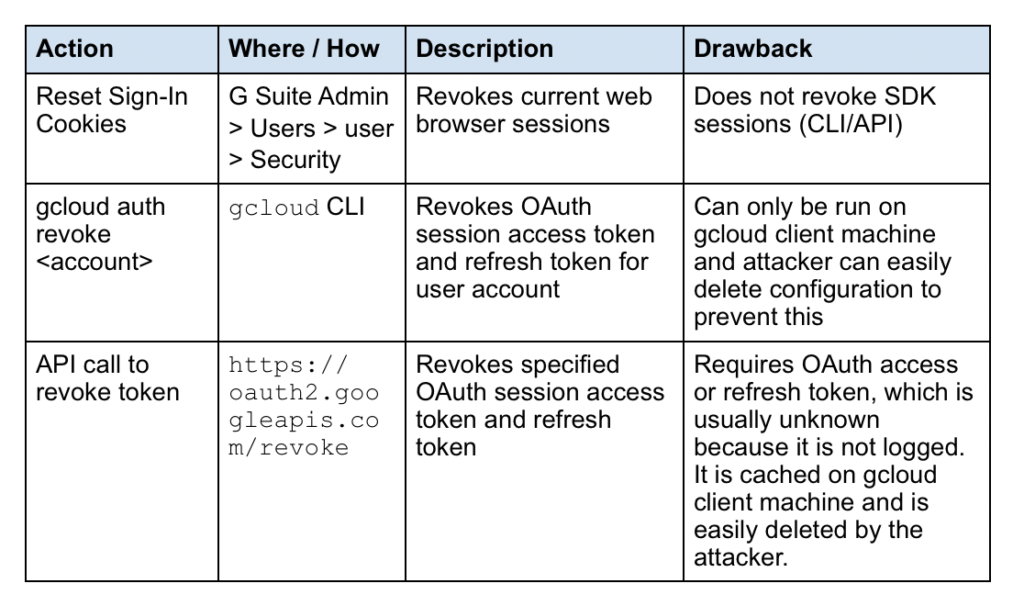
GCP OAuth Token Hijacking in Google Cloud—Part 2 - Netskope
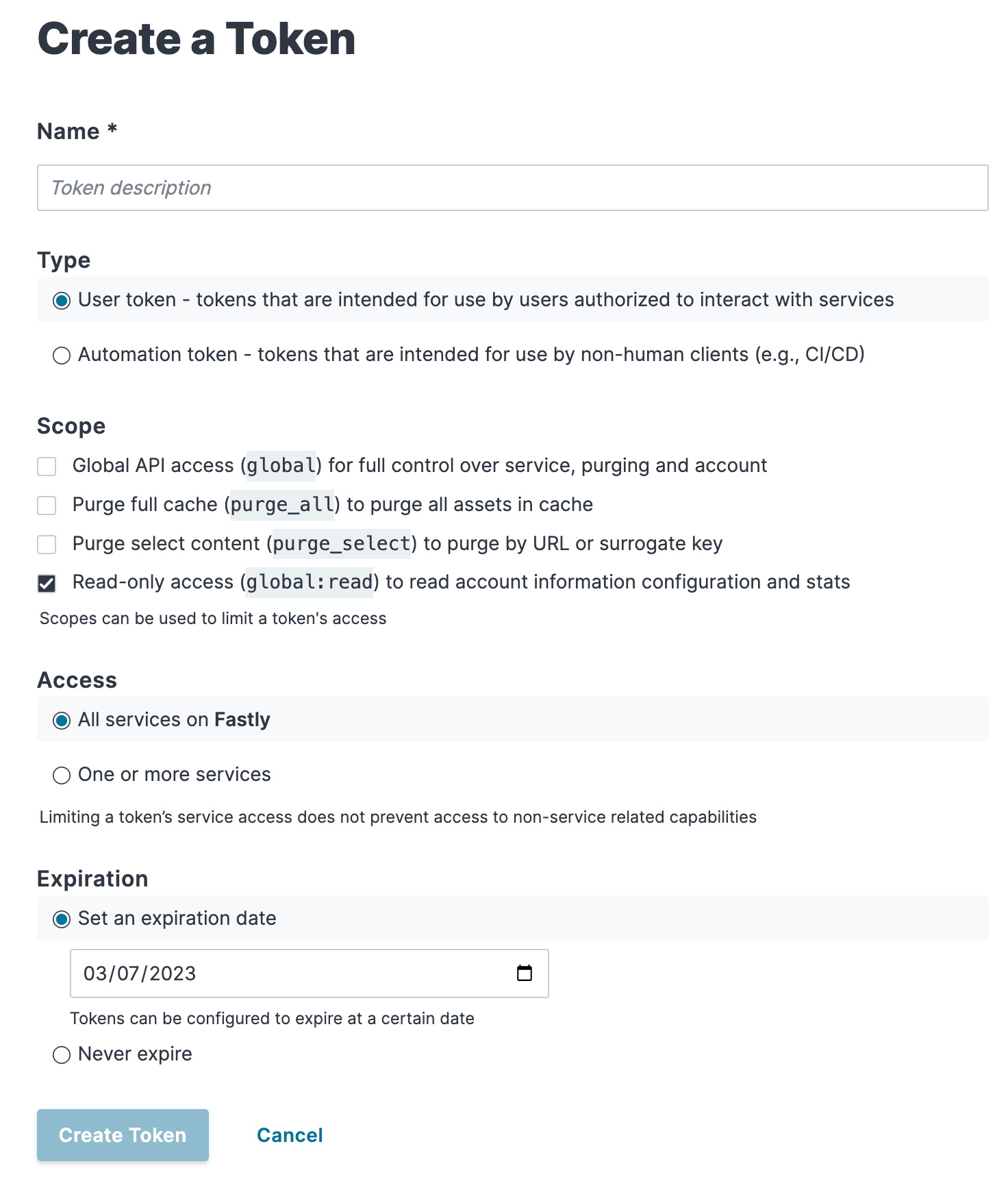
Using API tokens Fastly Help Guides
Recommended for you
-
 What is a token?02 Jun 2024
What is a token?02 Jun 2024 -
 Cryptocurrency Coins vs Tokens: Key Differences Explained [202302 Jun 2024
Cryptocurrency Coins vs Tokens: Key Differences Explained [202302 Jun 2024 -
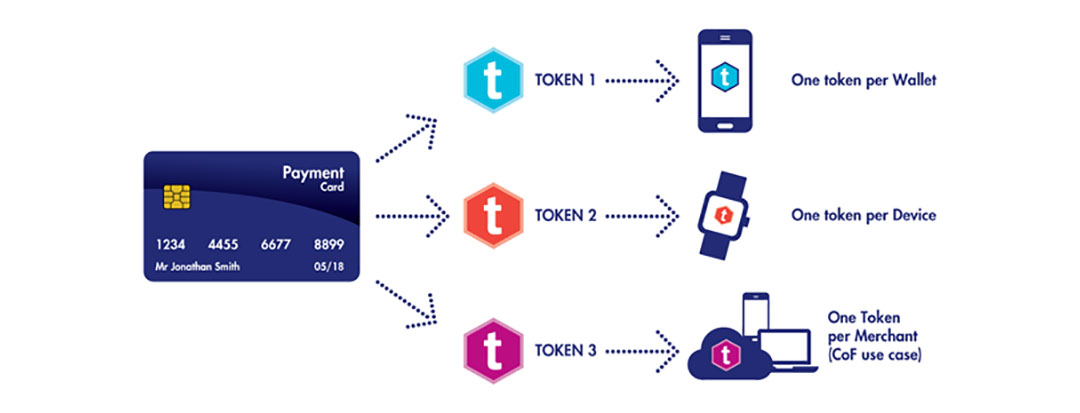 What is payment tokenization? (Updated)02 Jun 2024
What is payment tokenization? (Updated)02 Jun 2024 -
 How to Buy Bitcoin ETF Token - Beginners Guide02 Jun 2024
How to Buy Bitcoin ETF Token - Beginners Guide02 Jun 2024 -
 Map · The Lost Caverns of Ixalan Tokens (TLCI) #17 · Scryfall02 Jun 2024
Map · The Lost Caverns of Ixalan Tokens (TLCI) #17 · Scryfall02 Jun 2024 -
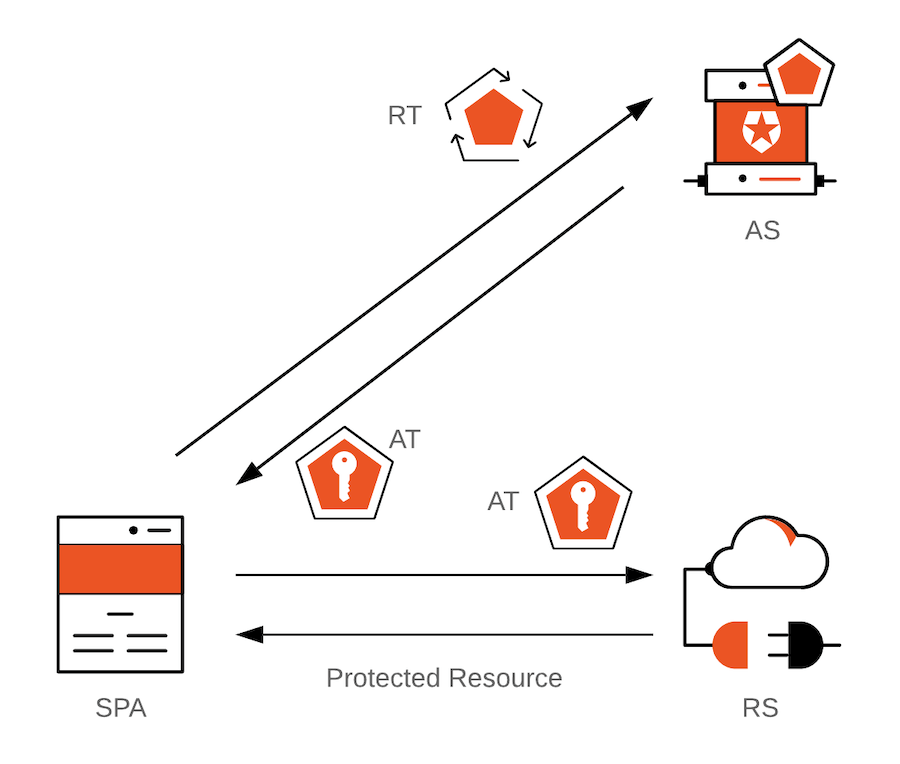 What Are Refresh Tokens and How to Use Them Securely02 Jun 2024
What Are Refresh Tokens and How to Use Them Securely02 Jun 2024 -
 Render Token (RNDR) - The Giving Block02 Jun 2024
Render Token (RNDR) - The Giving Block02 Jun 2024 -
 Token Features - Roll20 Wiki02 Jun 2024
Token Features - Roll20 Wiki02 Jun 2024 -
 What is a Token? (Explained Simply)02 Jun 2024
What is a Token? (Explained Simply)02 Jun 2024 -
 Token2, Token2 c202 hardware token - 10 pack, TOKEN2 MFA Products and Services02 Jun 2024
Token2, Token2 c202 hardware token - 10 pack, TOKEN2 MFA Products and Services02 Jun 2024
You may also like
-
 Magic Sticky Mat for Diamond Painting DIY Tools Diamonds Tray Holder Idea for Holding Tray 5D Diamond Embroidery Accessories02 Jun 2024
Magic Sticky Mat for Diamond Painting DIY Tools Diamonds Tray Holder Idea for Holding Tray 5D Diamond Embroidery Accessories02 Jun 2024 -
 Shannon Fabrics Double-Sided Crosshatch Cloud Cuddle Navy Minky Fabric 1 Yard02 Jun 2024
Shannon Fabrics Double-Sided Crosshatch Cloud Cuddle Navy Minky Fabric 1 Yard02 Jun 2024 -
 PC power button cover to keep my cats from turning my computer off02 Jun 2024
PC power button cover to keep my cats from turning my computer off02 Jun 2024 -
 Heart Silicone Resin Mold Large ,medium, Small or Xsmall02 Jun 2024
Heart Silicone Resin Mold Large ,medium, Small or Xsmall02 Jun 2024 -
 Extra Large (5 Gallon) Divided/Compartment Cleaning Utility Caddy Tote — Joey'z Shopping02 Jun 2024
Extra Large (5 Gallon) Divided/Compartment Cleaning Utility Caddy Tote — Joey'z Shopping02 Jun 2024 -
 MCS 12x12 Inch Scrapbook Expansion Page Refills, 6 Count (89967602 Jun 2024
MCS 12x12 Inch Scrapbook Expansion Page Refills, 6 Count (89967602 Jun 2024 -
 Reviews for BEHR 1 gal. Empty Plastic Paint Bucket with Pour Spout02 Jun 2024
Reviews for BEHR 1 gal. Empty Plastic Paint Bucket with Pour Spout02 Jun 2024 -
 EVEBOT Coffee Printer 3d Printer Latte Art Coffee Printer Printing Machine for Coffee Shop - AliExpress02 Jun 2024
EVEBOT Coffee Printer 3d Printer Latte Art Coffee Printer Printing Machine for Coffee Shop - AliExpress02 Jun 2024 -
 LCOZX Diamond Art Painting, DIY Diamond Art Painting Kits for Adults, Art Love Paint by Numbers for Adults, Home Leisure, Wall Decoration, Round Diamonds, Pattern Measures 12x16 inch, No.102 Jun 2024
LCOZX Diamond Art Painting, DIY Diamond Art Painting Kits for Adults, Art Love Paint by Numbers for Adults, Home Leisure, Wall Decoration, Round Diamonds, Pattern Measures 12x16 inch, No.102 Jun 2024 -
 How to Safely Operate Your Car Tow Dolly02 Jun 2024
How to Safely Operate Your Car Tow Dolly02 Jun 2024